Hey guys, differently from what I said before, today I will make a pause in the Google Hacking theme just to answer online a question made in person by a friend when I talked him about what we discussed here on Day 5 of 100, concerning the correlation of the Wifi router MAC address/BSSID and its default password. So, this friend of mine asked me: “Is there any way to discover a Wifi router MAC address WITHOUT BEING CONNECTED to it?”.
First and quick answer: obviously yes, with a little remark: we are talking about BSSID, and CONCEPTUALLY it is not exactly equal to MAC address (for a further explanation, check this). However, in order to make it simpler, I shall vary its name through this post - using both MAC address and BSSID - just because I’m stubborn as hell.
I will cite here two (of lots of) methods for discovering such address - one of them, well-known in hacker culture world, and the other with a self open source solution in Python. So, lets see these two solutions.
Method 1 - Classic “h4x0r” airmon-ng + aireplay-ng borgin method
I called this a classic ‘h4x0r’ method just because it might seem simple to any script kiddie perform by following online “how-to-_honk_-my-neighbour-wifi” tutorial (pun intended). It only demands two or three basic steps, depending on your current Linux distro (always use Linux) configuration:
-
Install Aircrack-ng suite with
sudo apt install aircrack-ng[skip this step if you already have it installed or read this masterpiece if you don’t know what aircrack-ng is] - Enable monitor mode on your wireless interface with airmon-ng:
- Skipping some basic steps since this is not the main theme for this post, this procedure is easily performed with
sudo airmon-ng start <wireless_interface_name>; - To check your wireless interface name, just type
sudo airmon-ngand check it out; regular names are wlan0, wlp2s0 and others; - Let’s assume your wireless interface name is wlan0, for instance. After starting monitor mode, its name might change to wlan0mon.
- Skipping some basic steps since this is not the main theme for this post, this procedure is easily performed with
- Start package capturing of raw 802.11 frames on the wireless interface under monitor mode with airodump-ng:
- Once again, skipping some basic steps because of reasons, just type
sudo airodump-ng start wlan0mon(since we assumed wlan0 was your wireless interface name and wlan0mon its monitoring mode name), press enter and hold;

- Once again, skipping some basic steps because of reasons, just type
“HOLD… HOLD… HOOOOLD… HOOOOOOOOOOLD… NOOOOOOWWWW!“ - William Wallace, Braveheart (1995)
- After some time, you can stop airodump execution and there you go: a list of BSSID/ESSID of reachable wireless networks. See an example (taken from the internet) for an output of airodump-ng:
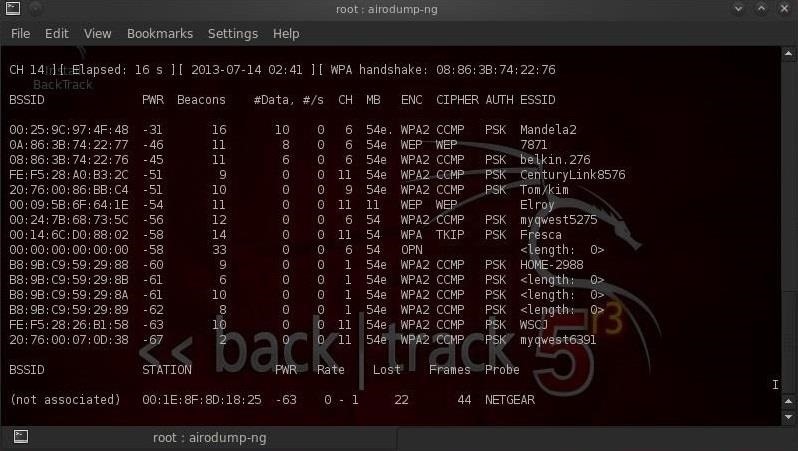
- FTR #1: that is one of the simplest things someone can do with airodump-ng. For instance, if you have a GPS receiver connected to the computer, airodump-ng is capable of logging the coordinates of the found access point. Learn more here.
- After this procedure, execute
sudo service network-manager restartto return your wireless interface from monitor to regular mode.
Method 2 - Self open source solution in Python
I have spent some time on this subject and developed a simple Python3 routine that uses Scapy 802.11 packets handling features to capture BSSID/ESSID of reachable wireless AP signals. In order to run it, install scapy by running:
sudo pip3 install scapy
After that, feel free to run the code ahead under root privilege:
from scapy.layers.dot11 import Dot11
from scapy.sendrecv import sniff
def sniffer(pck):
if pck.haslayer(Dot11):
if pck.type == 0 and pck.subtype == 8: # Understand why in => https://en.wikipedia.org/wiki/Beacon_frame
print("AP BSSID: %s - SSID: %s" %(pck.addr2, pck.info))
sniff(iface="wlan0", prn=sniffer, store=0) pass sniff(iface="mon0", count=0, prn=Handler, store=0) # don't forget sudo rfkill unblock wifi && sudo airmon-ng start wlan0 before this
That code shall print a list of AP BSSID/ESSID similar to those in airodump-ng. In case of issues, check dependencies, privileges and other obstacles; it works really fine for me. =P
And, in the end, why is that important at all? For now, let’s just consider a Brazilian particular case for default wireless network naming in main internet providers: GVT/Vivo and NET/Claro use part of the router BSSID/MAC as its default wireless network names! By knowing this fact and discovering the upmentioned address, and also by hoping someone who did not change the wifi default name might not have changed its default password one might easily crack the wifi password simply by typing the last 8 characters of the router BSSID.
For instance, let’s say that after using airodump-ng, I get as an reachable BSSID/ESSID a wireles network named “NET_2GB8373B” and addressed as “98:1E:19:B8:37:3B”. For gods sake, the default password for that network totally is 19B8373B (FTR #2: I would try that even for the network on the example image above with ESSID “HOME-2988“ and BSSID B8:9B:C9:59:29:88. See the pattern?!)
So, this is a tested and approved method for “guessing” passwords of wireless networks with default ESSIDs through two different methods. Hope you all enjoy this post and next time (I will work to keep schedule and post until Monday..), I promise I will talk about Google Hacking. See you then!
#100daysofcode #day7of100 #programming #coding #code #python #developer #coder #programmer #peoplewhocode #hacking #ethicalhacking #hacktheplanet #macaddress #bssid #wifi #airodump #scapy